Did you know that Microsoft Word can actually edit PDF files? Well… the most recent version of it can, anyway. Since Adobe Acrobat can be a considerable investment for each and every one of your employees, you can instead turn to the tried and true Microsoft Word for this purpose. We’ll show you how you can do this (as long as you have the most recent version of MS Word).
Open the PDF
First, you’ll need to open the PDF. To do this, open up Microsoft Word and select Open Other Documents from the left-hand menu.
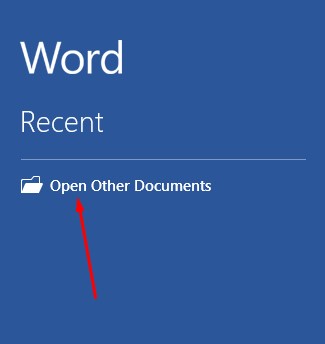
This brings up the Open menu. Next, you want to click on Browse.
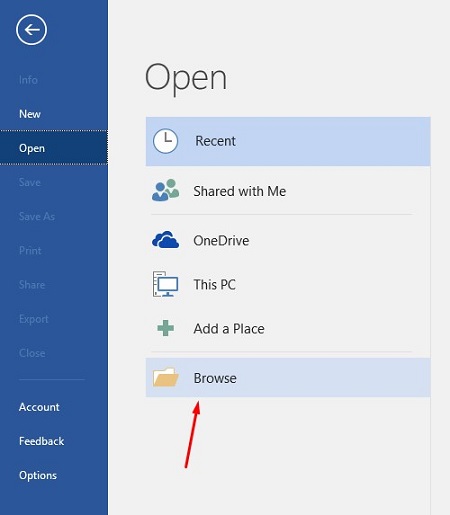
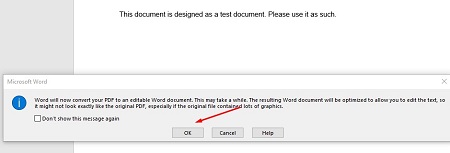
Another message will appear telling you that Word will convert the PDF to an editable Word document. If this sounds fine, click on OK.
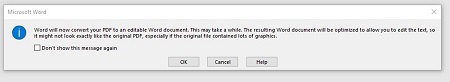
Your PDF should open up in Word now, but you might notice that there is still a yellow bar at the top of the screen that says PROTECTED VIEW. This is meant to secure your software from opening anything dangerous. If you can trust the document, click the Enable Editing button.
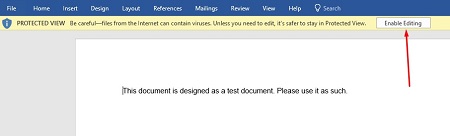
Once you press the button, another notification will show you that Word will convert the PDF to an editable Word document. To close this message, just click on the checkboxor click OK.
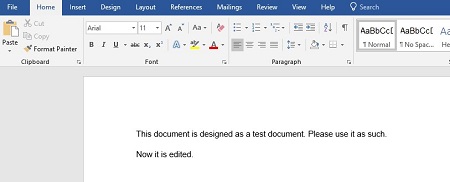
You can now edit your PDF.
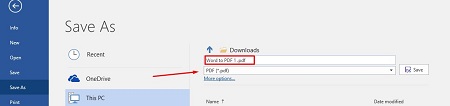
Once you’re done, you can save the file back to a PDF format. To do this, select File > Save As and set the type to PDF from the dropdown menu under the assigned file name. You will have to rename the document slightly to save it to a file folder.
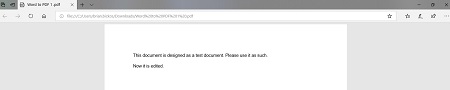
Once you’re done, your edited PDF will open in Microsoft Edge, or whatever your default PDF viewer happens to be.
What are some other cool features of Microsoft Word that you would like us to cover? Let us know in the comments, and be sure to subscribe to our blog.
![]()









