The National Institute for Standards and Technology (NIST) has released Special Publication 800-63B, titled Digital Identity Guidelines. The document outlines major changes to the ways password security should be approached and leaves a lot of what network administrators and software developers have implemented recently to be wrong Today, we’ll take a look at the publication, and try to make sense of the sudden change of course.
NIST is a non-regulatory federal agency that works under the umbrella of the U.S. Department of Commerce. Its mission is to promote U.S. innovation and competitiveness by advancing a uniform measurement standard. Many NIST guidelines become the foundation for best practices in data security. As a result, any publication they produce having to do with cyber or network security should be considered.
A Look at SP 800-63B
The newest password guidelines are a swift about-face in strategy as compared to previous NIST suggestions. Instead of a strategy of ensuring that all passwords meet some type of arbitrary complexity requirements, the new strategy is to create passwords that are easier and more intuitive. Here are some of the highlights:
- Passwords should be compared to dictionaries and commonly-used passwords
- Eliminate or reduce complexity rules for passwords
- All printable characters allowed, including spaces
- Expiration of passwords no longer based on time password has been in use
- Maximum length increased to 64 characters.
Basically, the new guidelines recommend longer passphrases to the complex passwords as they are hard for people to remember, and even with complexity rules in place, it was becoming increasingly easy for algorithms to crack passwords (seen in the comic strip below).
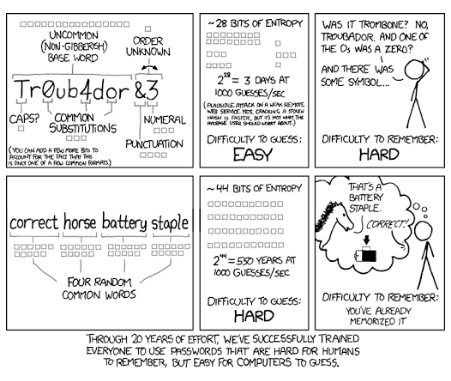
As stated before, NIST is not a regulatory organization, but federal agencies and contractors use NIST’s information in order to set up secure computing environments in which to display, store, and share sensitive unclassified information.
In making these changes to password strategy, NIST is now considering the fact that many industry professionals knew: a password you can’t remember may be secure, but if it’s so secure that you have to rely on third-party software to utilize it, it’s not really that effective at mitigating risk. NIST now looks at the passphrase strategy, along with two-factor authentication as the go-to risk management strategy. SMS-based two-factor authentication was not mentioned in the final report but has come under scrutiny as it has contributed to multiple hacks in recent times.
The NIST also explicitly commands that network administrators be mindful to forbid commonly used passwords; effectively creating a blacklist of passwords. The new guidelines also suggest that users shouldn’t be using the password hints or knowledge-based authentication options; a common practice among banking and FinTech applications to this day. We’ll see if there is a strategic alteration in these companies’ practices as the new NIST guidelines become best practices.
If you are looking for more information about best password practices and data security, the IT experts at XFER are here to help. Call us today at 734-927-6666 / 800-GET-XFER to have your password strategy assessed by the professionals.
Comic by XKCD.
![]()


