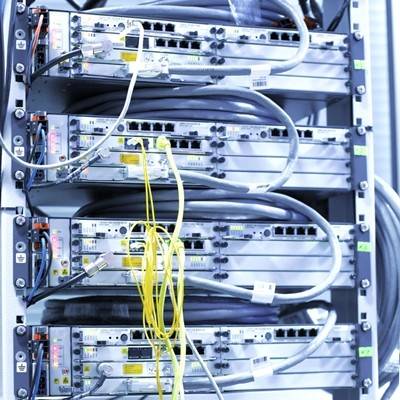
If you have been following international news headlines with stories like WikiLeaks spreading confidential documents, and recent revelations about a US surveillance scandal, it kind of feels like we are in the middle of Spy vs. Spy. As nations look for stronger security solutions to protect themselves, Russia is looking to older technology to keep their communications safe.
Customer Login
Don’t Leave Your Business Exposed
![]()
Our cybersecurity risk assessment will reveal hidden problems, security vulnerabilities, and other issues lurking on your network.
Contact Us
Learn more about what XFER can do for your business.
XFER Communications, Inc.
31478 Industrial Road Suite 200
Livonia, Michigan 48150